Front door vrfs in a tunneled environment are really quite cool.
Front door vrf ipsec.
Defining the pre shared key crypto keyring dmvpn vrf dmvpn pre shared key address 0 0 0 0 0 0 0 0 key cisco when you are using a front door vrf you can t define the key using the old crypto isakmp key command.
If no vrf aware config is used everything is done in the global vrf and all interfaces are in the global vrf.
Front door vrf or outside vrf the vrf that contain the encrypted traffic.
The routing instance that is used if no specific vrf is defined.
Since the isakmp policy and the ipsec transform set are exactly the same as in regular ipsec dmvpn i won t focus on those.
Idea here is to have underlay network running in a vrf often called fvrf or front door vrf.
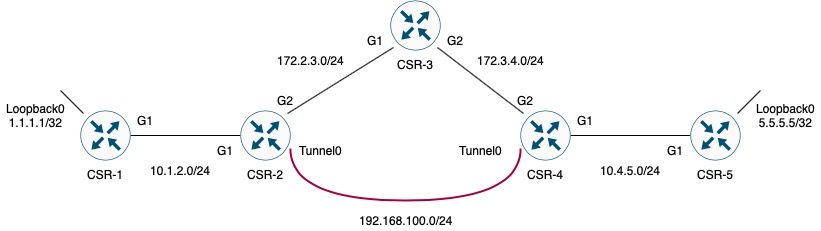
In this post i want to show how to configure dmvpn with ipsec with tunnel source destination ips located in a separate vrf.
In the diagram below what this means is that i have the wan facing physical interface of the dmvpn tunnel end points in a vrf but the tunnel over it is not in a vrf but is in the.
The outer encapsulated packet belongs to one vrf domain called the front door vrf fvrf while the inner protected ip packet belongs to another domain called the inside vrf ivrf.
Cisco s validated design cvd for iwan suggests the use of front door vrfs in an iwan environment.
Under the geographic separation scenario eompls would normally be used to link the two ip networks.
Dmvpn and ipsec with front door vrf 24 february 2017 9 min read.
Stated another way the local endpoint of the ipsec tunnel belongs to the fvrf while the source and destination addresses of the inside packet belong to the ivrf.